|
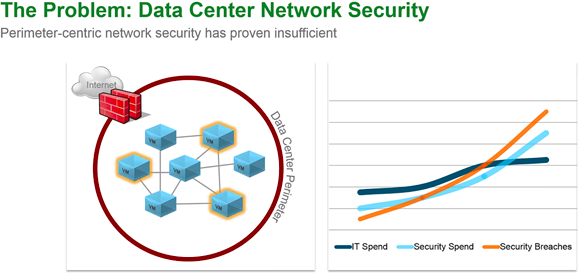
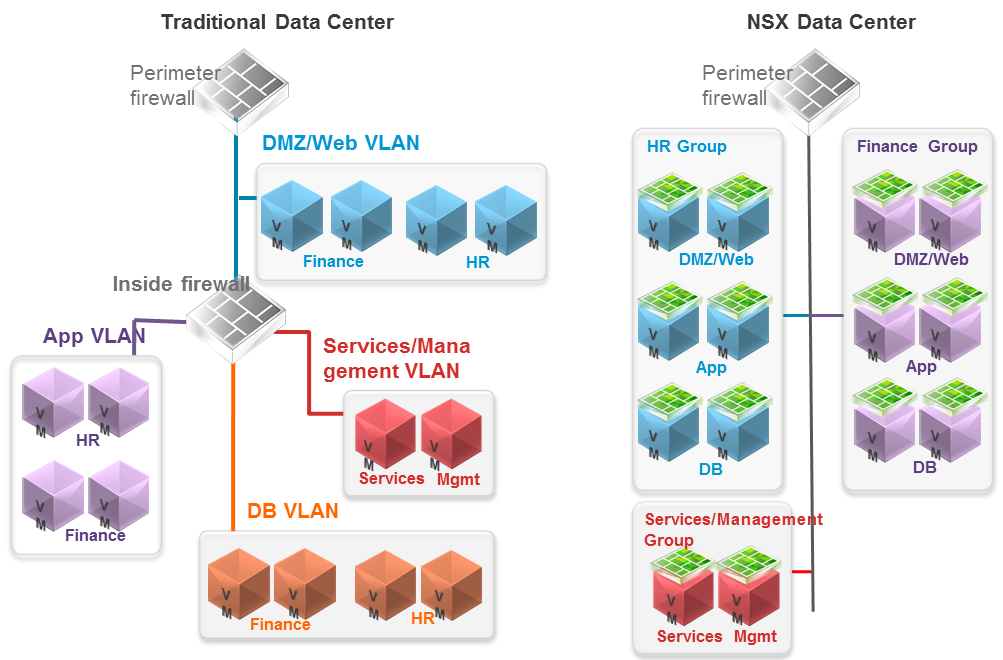
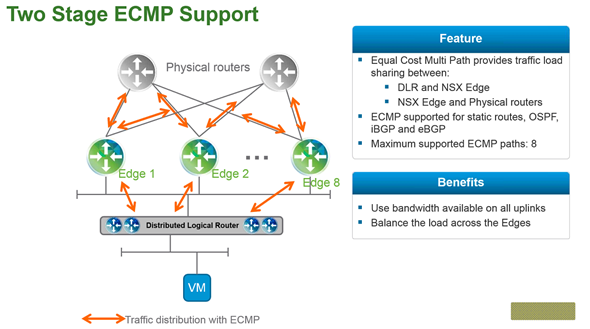
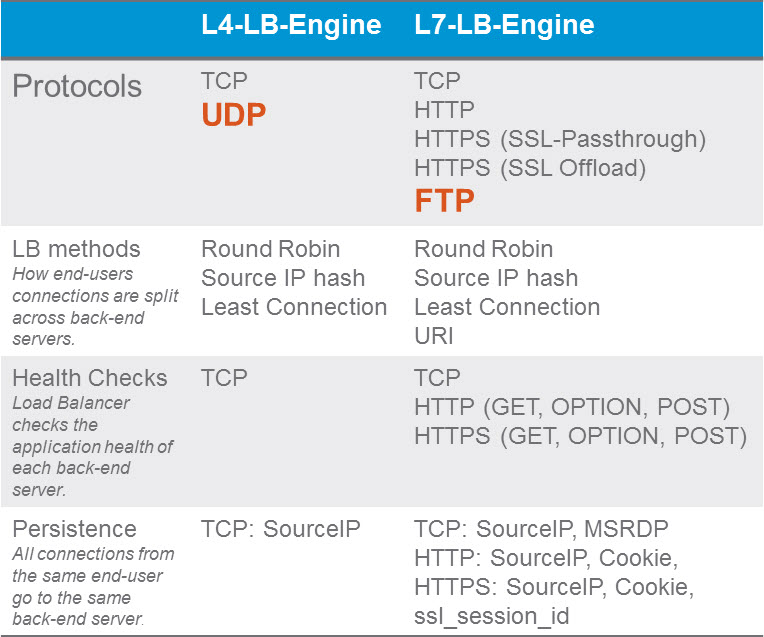
Segmentation It can be extremely difficult to secure and maintain security in your production environment. The traditional security model focuses on the perimeter defense but continued security breaches show that this model is not affective. Firewall can be deployed at each VM, but that proves to be unmanageable. With NSX 6.1 it is possible to micro segment your network, so that only traffic that is allowed can travel through the network between virtual machines. Traditionally, network segmentation is a function of a physical firewall or router, designed to allow or deny traffic between network segments or tiers. The traditional processes for defining and configuring segmentation are time consuming and highly prone to human error, resulting in a large percentage of security breaches. Implementation requires deep and specific expertise in device configuration syntax, network addressing, application ports and protocols. Network segmentation is a core capability of NSX. A virtual network can support a multi-tier network environment, meaning multiple L2 segments with L3 segmentation or micro-segmentation on a single L2 segment using distributed firewall rules. These could represent a web tier, application tier and database tier. Physical firewalls and access control lists deliver a proven segmentation function, trusted by network security teams and compliance. Confidence in this approach for cloud data centers, however, has been shaken, as more and more attacks, breaches and downtime are attributed to human error in to antiquated, manual network security provisioning and change management processes. In a virtual network, network services (L2, L3, ACL, Firewall, QoS etc.) that are provisioned with a workload are programmatically created and distributed to the hypervisor vSwitch. Network services, including L3 segmentation and fire-walling, are enforced at the virtual interface. Communication within a virtual network never leaves the virtual environment, removing the requirement for network segmentation to be configured and maintained in the physical network or firewall. Two Stage ECMP Equal cost multi path (ECMP) routing for distributed logical routers and NSX Edges has been added to 6.1. This gives NSX the ability to support ECMP between the Distributed Logical Router (DLR) and the NSX Edges to the physical network. This is limited to 8 ECMP paths. With this new feature you can better utilize bandwidth by way of multiple NSX Edges and their respective uplinks. Load Balancing Every NSX Edge has the ability to provide load balancing which can provide support for load balancing policies of IP hash, least connection, round robin and URI. NSX 6.1 includes the ability to load balance TCP, UDP and FTP. Firewall Enhancements
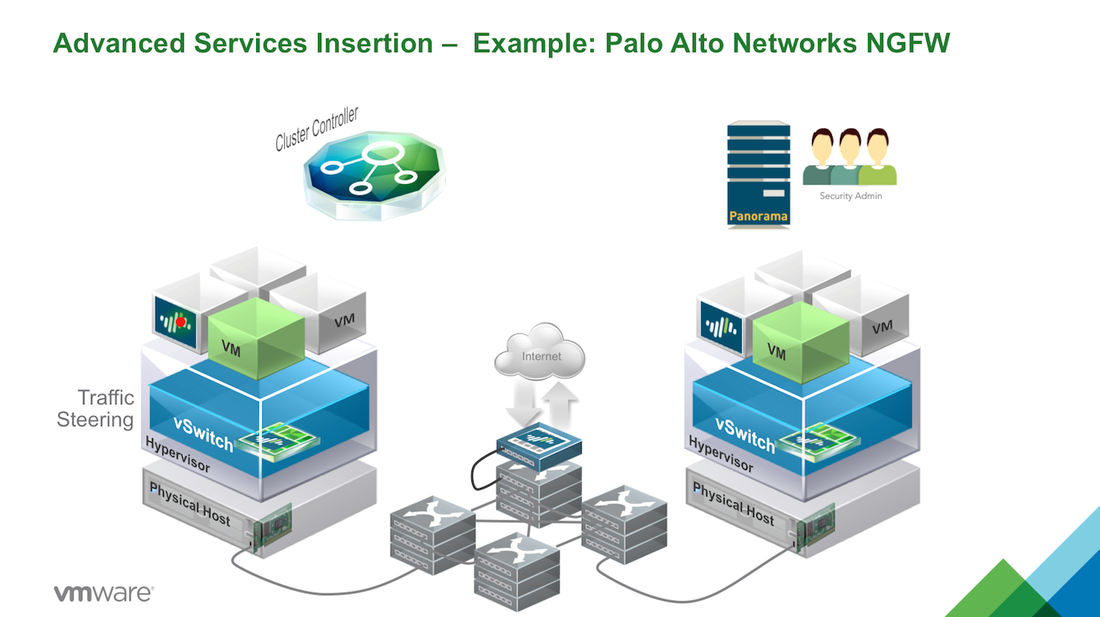
VMware NSX platform to distribute the Palo Alto Networks VM-Series next generation firewall, making the advanced features locally available on each hypervisor. Network security policies, defined for applications workloads provisioned or moved to that hypervisor, are inserted into the virtual network’s logical pipeline. At runtime, the service insertion leverages the locally available Palo Alto Networks next-generation firewall feature set to deliver and enforce application, user, context-based controls policies at the workloads virtual interface. VMware NSX provides a platform that allows automated provisioning and context-sharing across virtual and physical security platforms. Combined with traffic steering and policy enforcement at the virtual interface, partner services, traditionally deployed in a physical network environment, are easily provisioned and enforced in a virtual network environment, VMware NSX delivers customers a consistent model of visibility and security across applications residing on both physical or virtual workloads.
0 Comments
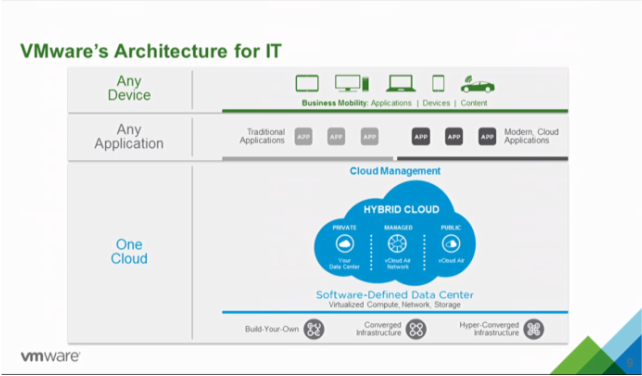
VMware CEO Pat Gelsinger announced a new hybrid cloud strategy today along with a series of product updates, including a new version of vSphere, VSAN, VVOLs, a distribution of OpenStack and integrations of NSX with vCloudAir. The new vision laid out by VMware CEO Pat Gelsinger is one of a "Seamless and Complete Picture," of Any Device, Any Application and One Cloud. VMware spoke with their customers and found that they are looking for three key areas when it comes to IT:
With a foundation of vSphere 6.0 and new features including One Management, whether on premise or off, NSX built into vCloudAir, VSAN, and VVOLs the architecture is designed to bring a unified cloud. CEO Pat Gelsinger states that "customers increasingly need a software-defined infrastructure to enable the level of speed, agility and flexibility to respond to the challenges of IT." VMware vSphere 6.0 VMware is raising the bar again with more than 650 new features in vSphere 6.0. Some of the newly announced features include:
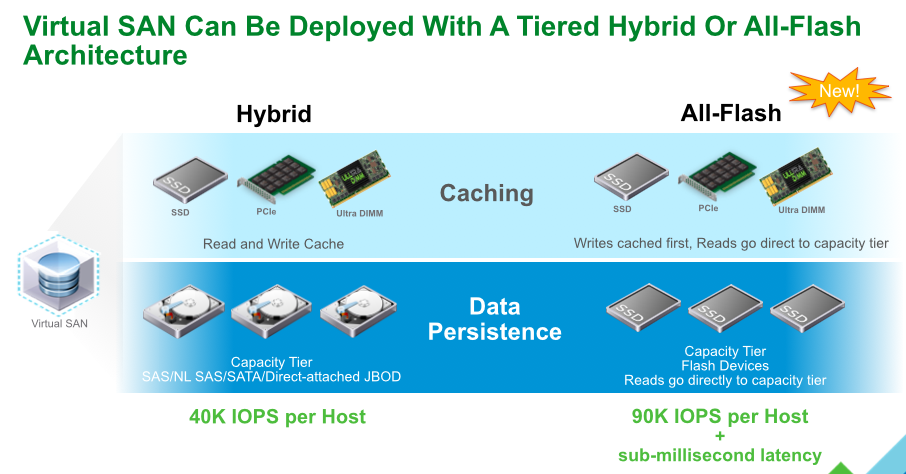
VMware VSAN With significant improvements in scale and functionality new features in VSAN include:
VVOLs vSphere Virtual Volumes enable native virtual machine awareness on third-party storage systems along with VMware's Instant Clone technology for cloning and provisioning thousands of virtual machines to make a new virtual infrastructure.
OpenStack OpenStack distribution will enable smaller IT departments with "little or no OpenStack or Linux experience" to deploy an OpenStack cloud within minutes.
VMware NSX NSX will enable customers to achieve unprecedented security and isolation in a cloud with new features and enhancements.
VMware's Any Device, Any Application and One Cloud approach lets customers utilize multiple clouds to securely accelerate IT while managing through a single environment.
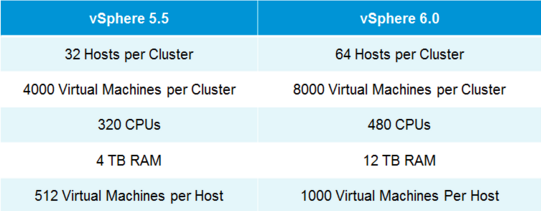
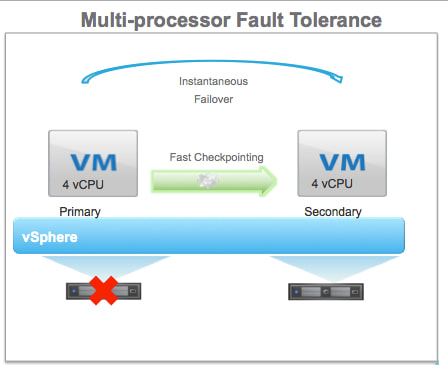
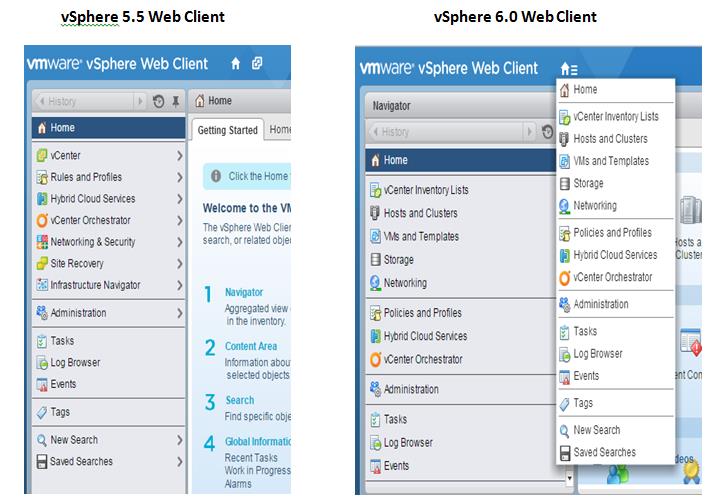
VMware vSphere 6.0 is the next major release since 5.5 and with any major release it is packed with new features and enhancements along with increased scalability. This version comes with some big improvements to VSAN which I'll discuss below. Host ImprovementsIn vSphere 5.5 the maximum supported host memory was 4TB, in 6.0 that jumps up to 12TB. Also, in vSphere 5.5 the maximum supported number of logical (physical) CPUs per host was 320 CPUs, in vSphere 6.0 that is increased to 480 CPUs. The last improvement to the hosts is the maximum number of VMs per host, increasing from 512 in 5.5 to 1000 VMs per host in 6.0 This gives the ability to create some monster VMs. Fault Tolerance IprovementsFault Tolerance (FT) was introduced in vSphere 4. FT provides protection of VMs by preventing downtime in case of a host failure. FT has never been greatly used due to its design preventing anyone that required multiple CPUs from utilizing FT. FT now supports more than one vCPU and moves from 1 vCPU to 4 vCPU support. The design of FT has changed were the way FT worked in the past you had 2 VMs on separate hosts, one as a primary and the other as the secondary. The VMs relied on shared storage. In vSphere 6.0 this has now changed allowing for each VM to have their own virtual disk that can be located on different storage. VMware also improved the prior limitations with snapshot support for FT. Having separate disks helped with this issue. Now that there is built in support for snapshotting a FT VM, you can back it up. Prior to this admins found themselves challenged with how to perform agentless backup while maintaining FT for the VMs requiring it. In order to backup the VMs requiring FT prior to 6.0 you had to install a backup agent and backup the vm in a more traditional manner. vSphere Web Client ImprovementsThe web client has never been a favorite of admins and with the release of vSphere 6.0 VMware has made some great performance and usability improvements. Performance Improvements:
Usability Improvements:
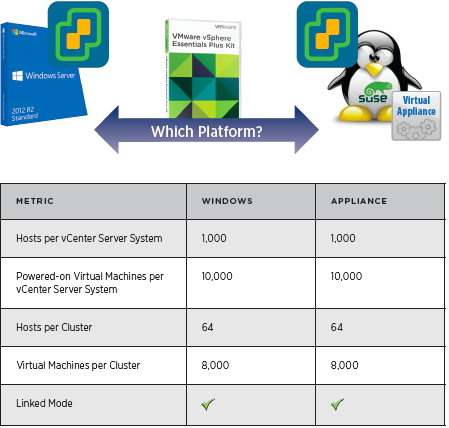
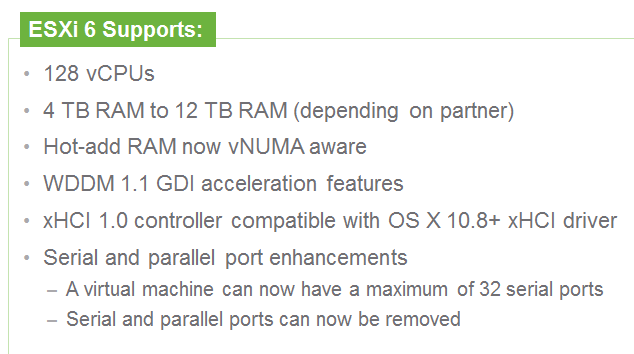
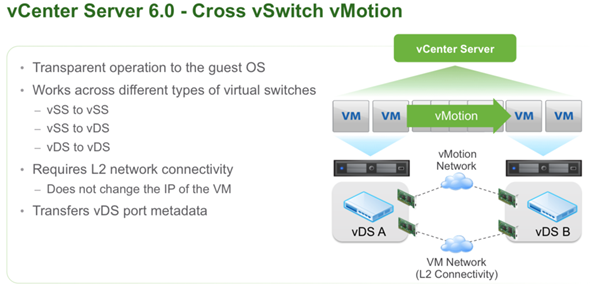
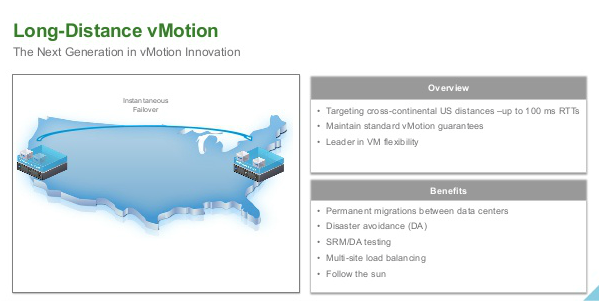
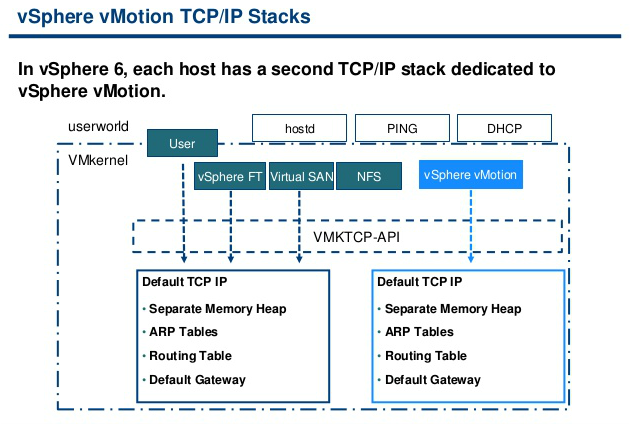
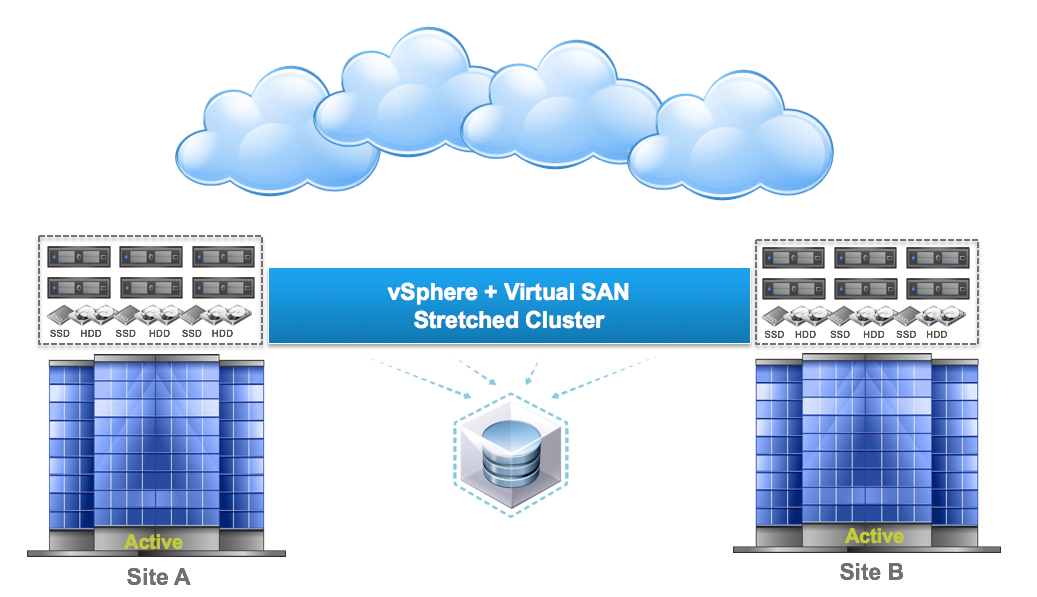
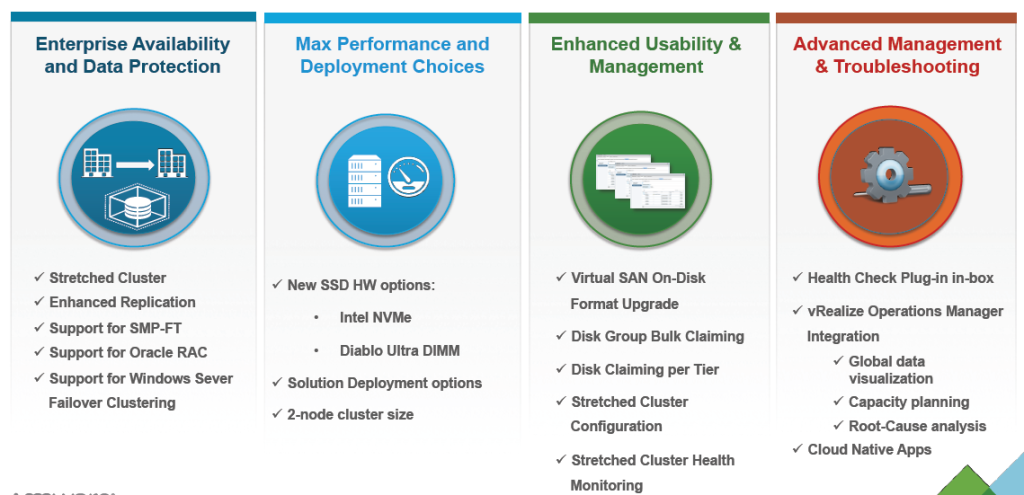
vCenter Server Appliance ImprovementsI have never been a fan of having to burn Microsoft Licenses in order to deploy vCenter or the amount of time it takes to spin up a Windows OS to support it for both the application and SQL database. I loved it when VMware came out with the appliance for an easy ova deployment but the limitations in scalability and support have been the main driving factor for admins to not deploy this in their environments. now in vSphere 6.0 the VCSA is fully scalable to the same limits that the vCenter Server on Windows scales to. This now means that the VCSA can support 1,000 hosts, 10,000 VMs and now linked mode. VM Improvements in 6.0Back in vSphere 5.5 a VM could be configured with up to 64 vCPUs and now in 6.0 that maximum has doubled to 128 vSPCUs. That is a crazy amount of vCPU. Another increase for the VM is around serial ports. VMware saw a need for this and has increased from 4 to 32 ports that can be configured on a single VM. If you don't have a need for them then you can remove the serial ports and parallel ports as needed. vMotion!!There have been a lot of new enhancements with vMotion technology to increase the range and capabilities of vMotioning a VM. You can now vMotion a VM between different types of virtual switches. VMs can be moved from a Standard vSwitch to a Distributed vSwitch without changing its IP address and without network disruptions. With the improvements to vMotion you can now vMotion a VM from a host located in one vCenter server to another host on a different vCenter server. There is no need for common shared storage between the the hosts and vCenter servers. This eliminates the traditional distance boundaries of vMotion. You can now move between data centers, regional data centers or continental. Another improvement to vMotion resides around latency requirements. In vSphere 5.5 the maximum vMotion latency was 10ms. In vSphere 6.0 that has increased to 100ms of latency. This allows for the vMotion of VMs between longer distances. VMware vMotion also includes its own TCP/IP stack which can cross layer 3 networks. Single Sign-on Improvementsn vSphere 6.0 VMware introduces a new Platform Services Controller. The controller groups together SSO, Licensing and Certificate authority. You can deploy this as embedded with vCenter server or external so that is completely independent of the vCenter server. Certificate management has always been a pain for Administrators. With the introduction of VMCA, you can now manage the provisioning and deployment of certificates for you vCenter servers, and ESXi hosts. vSANNow in its 3rd release as of August of 2015, VSNA 6.1 has already seen adoption across different industries and sizes. This release adds abilities around availability data protection and management. Virtual SAN Stretched Cluster allows admins to create a stretched cluster between two or more geographically separated data centers. Another feature of this release is Virtual SAN for Remote Office or Branch Offices. This provides the ability to deploy VSAN clusters for ROBO. You can now deploy large numbers of 2-node VSAN clusters that can be centrally managed from a central data center through one vCenter server.
Some other new features include:
|
RecognitionCategories
All
Archives
June 2024
|













 RSS Feed
RSS Feed