|
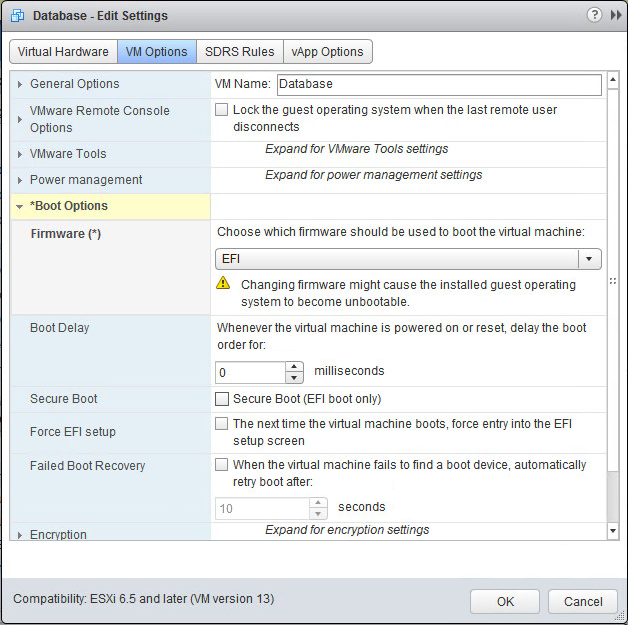
Security these days can be more of that traditional, needle in a haystack approach, than a true centric security approach to include analytics and alerting. VMware is again shifting to a new paradigm, and that was evident from all the products and messaging that came out of VMworld 2017. Security is on the forefront of all of our minds and VMware, as the leader in data center technologies, wants to lead the conversation and be the foundation that you are laying down to protect your data, along with adding significant value to you with their partnerships in the security space, like the new partnership announced with IBM around their security products like QRadar. With increasing attacks on our data centers, take Equifax for example, we must first look at one of our most significant portions of our security foundation, ESXi and work to secure that. We typically start with securing the physical and the edge, throw in some anti-virus and call it secure, but are we secure? When it comes to data center security, we must start with our foundation, ensure that we have designed it to follow recommended best practices, then evaluate the gaps, and add in products to get us the rest of the way there. This also includes following best practices for end-user access of the environments and not being "lazy" admins just to skip a few steps. We have to lean on trusted partners like Sirius that have developed a security practice that can help us navigate the waters of security because the landscape of security products is immense, as you can see from the picture below. So where do we begin? I believe that we must start with VMware. VMware is no longer just a hyper-visor running your vms, but the most integral part of your data center security strategy and if you don't get that foundation right, then the rest will crumble too. We must secure the infrastructure, build and architect the data. After we get the infrastructure secure we move into securing the entire ecosystem like controls, automation, validations and the security solutions. Last we must get back to the basics and as VMware's CEO, Pat Gelsinger stated, "Learn from sport teams who follow the basic regimen over and over again. Every major breach in the last five years that made headlines happened because a simple cyber hygiene wasn’t followed somewhere.” VMware is working with the government to set cyber hygiene standards for the tech industry to simplify the security solutions, as Gelsinger stated that, “The role of the governments globally in making stronger cyber policies is equally important to ward off data breaches." VMware has shifted to becoming a security centric company. With added features in their base product VMware ESXi 6.5 which represents a move toward "secure by default" and allows for a truly secure foundation to build the rest of the house. Let's take a look at these features. ESXi Secure Boot Secure Boot now leverages the capabilities of the UEFI firmware to ensure that ESXi not only boots with a signed bootloader validated by the host firmware but that it also ensures that unsigned code won’t run on the hypervisor. UEFI, or Unified Extensible Firmware Interface, is a replacement for the traditional BIOS firmware that has its roots in the original IBM PC. ESXi is comprised of a number of components. There is the boot loader, the VM Kernel, Secure Boot Verifier and VIBs, or “vSphere Installation Bundles”. Each of these components is cryptographically signed. You can read more about UEFI on wikipedia. Virtual Machine Secure Boot SecureBoot for VM's is simple to enable. Your VM must be configured to use EFI firmware and then you enable Secure Boot with a checkbox. (Note that if you turn on secure boot for a virtual machine, you can load only signed drivers into that virtual machine.) Secure Boot for Virtual Machines works with Windows or Linux. Enhanced Logging vSphere 6.5 introduces enhanced logging. Logs have traditionally been focused on troubleshooting and not security. Complete logs are now sent via the syslog stream for actions like "VM Reconfigure". Logs now contain more complete information, so notices of something changing you will now see what changed it changed from and what it changed to. You can then take actions against the information collected like rollback the change if it caused an issue. You will now see logs for actions like adding more memory to a vm. The associated logs will show you what it was before and after the change. From a security perspective you can see much more information like who made the change and with integrations with VMware Log Insight you will be able to parse the data quicker bringing you to faster remediation. VM Encryption/vMotion Encryption VM encryption works by applying a new Storage policy to a VM. It is Policy driven. You’ll be able to encrypt the VMDK and the VM home files. There are no modification within the guest OS. You can run different OS's like Linux, Windows, etc. and can be run from different storage like NFS, block storage, and VSAN. The encryption is happening outside of the Guest OS and the guest does not have access to the keys. The encryption works also for vMotion but both the source and the destination hosts must support it. After you apply an encryption policy to a VM, the VM receives a randomly generated key for each VM, and that key is encrypted with a key from the key manager. When you power-on the VM which has the Encryption Storage policy applied to, vCenter retrieves the key from the Key Manager, sends that to the VM encryption Module and unlocks that key in the ESXi hyper-visor. Encrypted vMotion works by having the randomly generated key added to the migration information, this is sent to each of the hosts participating in the vMotion process, the data going across the network is encrypted with the randomly generated key only for the migration process, and is one-time generated random key, which is generated by vCenter. vSphere Security Guide for vSphere 6.5 The new security guidelines have changed to a subset of things to focus on. This is changing from the traditional "Hardening Guides," from VMware to a "Security" guide. I will not go into the entire guide in this post but you can read the post from VMware here. Along with these new settings, government work, and a new security guide being introduced, I think its time to shift into the products that support VMware security model. The first of these is NSX. With organizations spending more on security than ever before, see Gartner, NSX becomes the next integral step to securing your production data center. I have written several blogs now on NSX so I will just write a quick recap as to what NSX is. VMware NSX provides a platform that allows automated provisioning and context-sharing across virtual and physical security platforms. Combined with traffic steering and policy enforcement at the virtual interface, partner services, traditionally deployed in a physical network environment, are easily provisioned and enforced in a virtual network environment, VMware NSX delivers customers a consistent model of visibility and security across applications residing on both physical or virtual workloads. To further enhance NSX VMware introduced at VMworld 2017, AppDefense. AppDefense adds data center threat detection and response to the micro-segmentation capabilities delivered by NSX. NSX prevents threats from moving freely throughout the network, while AppDefense detects anything that does make it to an endpoint and can automatically trigger responses through integrations with NSX and vSphere. The idea is to prevent, detect, and respond. AppDefense uses machine learning technology, were it learns application behavior and if the application deviates from that behavior, it is quarantined. This is very different from the traditional approach with anti-virus solutions. Anti-virus solutions use definitions to secure the vm. If a new attack has been brought to the attention of your provider then they will create a new definition, once they have had time to analyze it, and then you are responsible for pushing the new definition out to all you vms. This can cause a gap in your protection. VMware has a dedicated internal team responsible for developing and driving software security initiatives across all of VMware’s Research and Development organizations to reduce software security risks; The VMware Security Engineering, Communications & Response group (vSECR).
The vSECR group takes a full lifecycle approach to product security from product inception to product end of life. VMware, through vSECR, is committed to the ongoing security of their products and the safety of their customers data. VMware is also active in the greater security community, and is a member of SAFECode (the Software Assurance Forum for Excellence in Code) and BSIMM (Building Security In Maturity Model). For more details about VMWare product security, please refer to the VMware Product Security White Paper. You may also be interested in the following resources:
Lastly, remember to reach out to your VMware Partner, like Sirius, who can help you with security health checks, education, and help you gain confidence in your production data center environment(s) is configured correctly. Sirius can help you prevent, detect, and respond to security threats and secure your data.
1 Comment
Your comment will be posted after it is approved.
Leave a Reply. |
RecognitionCategories
All
Archives
April 2024
|











 RSS Feed
RSS Feed